Phishing trends according to the Anti-Phishing Working Group
 The Anti-Phishing Working Group issued the results of a survey they conducted in the first half of 2009, in which they sifted through data they collected and some provided by private sources and phishing feeds, to define the latest phishing trends.
The Anti-Phishing Working Group issued the results of a survey they conducted in the first half of 2009, in which they sifted through data they collected and some provided by private sources and phishing feeds, to define the latest phishing trends.
The news are mixed: some of them good, other bad. The good news is that the average uptime of all phishing attacks has dropped from 52 (in the second half of 2008) to 39 hours. That is an extremely significant statistic – it means that the mitigation efforts by ISPs and responders are producing results. Anti-phishing programs implemented by domain name registries can reduce the up-times of phishing attacks, and can reduce the number of malicious registrations made in top level domains:
Another good news is that the number of phishing attacks also dropped. 55,698 attacks were registered in this first half of the year. That’s 1,261 attacks less that in the last years’ second half.
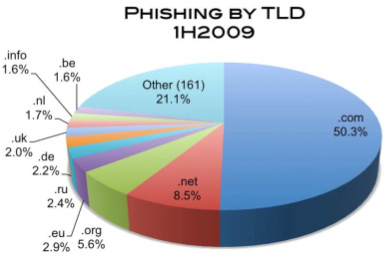
The bad news is that malicious domains registered by phishers represent about 14.5% of the domain names involved in phishing. The remaining 85.5% of the domains used for phishing were “compromised” or hacked domains.
Phishing most often takes place on compromised Web servers, where the phishers place their phishing pages unbeknownst to the site operators. This method gains the phishers free hosting and complicates take-down efforts because suspending a domain name or hosting account also disables the resolution of the legitimate user’s site.
It has also been discovered that 24% of all phishing attack during this period can be attributed to Avalanche, a phishing gang that obviously doesn’t slack off. The phishing site situated on their domains target financial institutions and on-line services, and they distribute malware by social-engineering.
These attacks involve domain names registered by the phishers, set up on name servers controlled by the phishers, and hosted on a fast-flux network of apparently compromised consumer-level machines. This fast-flux hosting makes mitigation efforts more difficult – calling the Internet Service Provider to get a site or IP blocked is not effective, and the domain name itself must be suspended at the registrar or registry level.
For more details, read this report.