Microsoft Edge: New browser, new risks for Windows 10
Microsoft Edge, the new browser in Windows 10, represents a significant increase in the security over Internet Explorer. However, there are also new potential threat vectors that aren’t present in older versions.
Integrated plug-ins
Microsoft Edge has now integrated two widely used plug-ins into the browser itself: Adobe Flash and a PDF reader. Flash has proved itself to be a significant security risk for many years. While we believe that users and sites should move away from it, the reality is that for the foreseeable future Flash won’t go away yet. Attacks targeting Flash will continue to be a problem, and having it as a built-in feature may pose risks down the road.
Similarly, an integrated PDF reader in the module windows.data.pdf.dll. This could also become a potential target for an attacker looking for a way into the Edge browser.
While these represent potential attack vectors, implemented properly they can remain relatively secure. Both Google Chrome and Mozilla Firefox have implemented integrated plug-ins without major problems; a proper implementation can reduce the risk from insecure plug-ins.
In addition, the integration of Flash means that updates to it can be pushed via Windows Update, reducing the risk of users running older Flash versions. (Note that this is not completely unprecedented: since Internet Explorer 10 on Windows 8, this has been the case already.)
Support for asm.js
One feature new to Edge is support for asm.js. This is a Mozilla-developed subset of JavaScript that has been designed to run faster than conventional code. In effect, it translates the C/C++/etc. code into JavaScript code, which can run much faster if the browser supports asm.js. The LLVM compiler is responsible for this action.

In other browsers, asm.js support has led to security problems. At 2015’s annual Pwn2Own competition, a vulnerability (CVE-2015-0817) in the Mozilla Firefox implementation of asm.js was used to successfully “own” that browser. Therefore, we cannot rule out the possibility that it could be a source of vulnerabilities in Microsoft Edge as well.
New extension model
Microsoft Edge will introduce improved extension support sometime after the launch of Windows 10. It is known that Chrome and Firefox extensions can be used by Microsoft Edge with relatively little modification, but other details have not been made clear.
These extensions will run in the AppContainer sandbox, but sandbox escape vulnerabilities can be used to evade this. In addition, the of malicious extensions cannot be ruled out – either they may be malicious from the start, or a legitimate extension can be modified with an update to become malicious.
However, the version of Edge that will be launched with Windows 10 does not have support for extensions yet.
Browser security comparison
The following tables compare the various features, protections, and attack surfaces of various browsers.
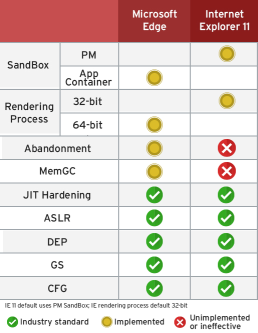
Although IE 11 supports the EPM sandbox, by default it only uses the PM sandbox. The IE 11 rendering process is also, by default, 32-bit.


Summary
Microsoft Edge represents a clear improvement compared to Internet Explorer 11. Specifically, the improved sandbox and exploit mitigation techniques make exploiting Edge more difficult than its predecessor. In addition, the dropping of unused legacy features reduces the possible attack vectors into the browser.
Overall, we believe that Edge has reached a security parity with the Google Chrome browser, with both markedly superior to Mozilla Firefox. However, multiple attack surfaces still remain which can be used by an attacker. Given the sophistication and demands on modern browsers, this may well be inevitable.

Author: Henry Li, Threats Analyst at Trend Micro.