Hacking Team scrambling to limit damage brought on by explosive data leak
Who hacked Hacking Team, the Milan-based company selling intrusion and surveillance software to governments, law enforcement agencies and (as it turns out) companies?
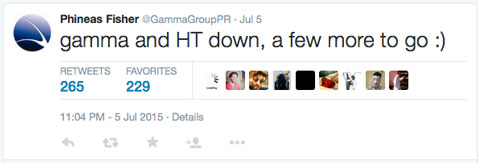
A hacker who goes by “Phineas Fisher” claims it was him (her? them?):

The hacker has also previously compromised UK-based Gamma International, another provider that sells their spying wares to governments, and which has also been named an “enemy of the Internet.” Phineas Fisher says there will be more similar hacks in the future:
In the meantime, Hacking Team is scrambling to minimize the damage this hack and data leak is doing to the company.
According to Motherboard‘s Lorenzo Franceschi Bicchierai, the company has sent out emails to all its customers, requesting them to shut down all deployments of its Remote Control System software (“Galileo”) – even though it seems they could do that themselves, as the customer software apparently has secret backdoors.
Perhaps they chose the first route because they hoped to keep that fact hidden from the customers? And because every copy of Hacking Team’s Galileo software is secretly watermarked, the leaked information could allow researchers to link a certain backdoor to a specific customer?
One of the reason for this shutdown request is that the data leaked contains source code of the company’s surveillance solutions, and they are worried that this information will allow targeted users to discover who’s spying on them.
“Another concern [by the wider security community] with this breach is that there is now source code available for some pretty nasty malware including what would appear to be functional exploit code,” points out Craig Young, Security Researcher, Tripwire.
“Although most users would not know what to do with the source code release, it would be surprising if we don’t very quickly start seeing underground malware authors branching and repackaging the HT malware and selling it without restriction. A more responsible action may have been for the hackers to release a document dump while sharing the malware source code only with reputable security vendors for the purpose of creating detection routines.”
All the stolen information was likely accessed via the compromised computers of Christian Pozzi and Mauro Romeo, two Hacking Team’s sysadmins. Christian Pozzi was apparently the first one who realized on Monday that the company was hacked, panicked and started threatening a researcher who pointed out his lousy password choices on Twitter. He also falsely claimed that the leaked torrent file contained a virus in an attempt to prevent people from downloading it.
The leaked cache is already being analyzed by many researchers and activists around the world, who are dropping the choicest morsels of information on Twitter and spreading them widely.
This is how we now know that the US FBI, DEA and Army, but also many governments with a poor track record of respecting human rights are/were Hacking Team customers, and that they have sold their software to the Sudan government (thus violating UN sanctions) and have been stonewalling the UN as they try to investigate the matter.
Also, that they can apparently bypass certificate pinning and the HTTP strict transport security mechanisms and were worried about EFF’s HTTPS Everywhere browser extension spotting their rogue certificates and send them to the EFF SSL Observatory, and that they used public exploits to compromise targets.
The Tor Project commented the leaked documents by saying that they knew Hacking Team was actively trying to break their software, but that so far they haven’t found any actual exploits.
Some of the leaked documents and screenshots seem to indicate that the hackers compromised the company’s infrastructure half a year ago, in January 2015, and possibly even earlier.
UPDATE: To get the latest updates on the Hacking Team story, go here.