Swift adoption of cloud and mobile drives insider threats
Bitglass surveyed 500 IT and security practitioners and found that 62 percent have seen an increase in insider threats over the last 12 months.
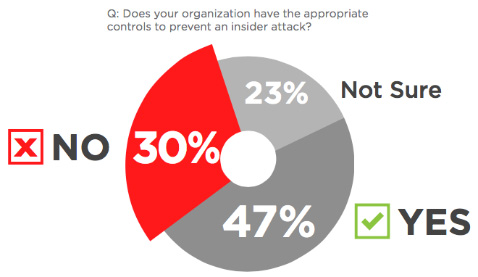
As more data leaves the network via cloud apps and mobile devices, the inability to protect these environments is cited as a top reason for the growth of insider threats. More specifically, respondents felt that insufficient data protection (54 percent), more data leaving the network (51 percent) and more devices with sensitive data (51 percent) are the top sources of insider threats.
The average data breach lasts 205 days (nearly 7 months), yet Bitglass found that only 11 percent of organizations believe it would take even 6 months to detect an insider threat. This is surprising, given that 70 percent of respondents said determining the actual damage of insider threats is difficult. In fact, 45 percent of enterprises had no idea how many insider threats actually occurred in their organization during the last year.

Charles Foley, Chairman and CEO of Watchful Software believes that not all breaches are done by ‘bad people’. “If you analyze the data, you see that some of the biggest risk is that people make honest mistakes. The fact is that technology has made it all too easy for information to move virtually anywhere in today’s world, which means that a simple errant ‘send’ button can put massively confidential information into the open domain. What we need to do now is to balance our former investments of ‘keep out technology’, such as firewalls, with ‘keep in technology’ such as classification, encryption, and rights management to ensure that our information is protected from harmful dynamics in either direction.”
Detecting insider threats has become more challenging as more applications and data migrate to the cloud. The applications most vulnerable to insider threats include cloud storage and file sharing (44 percent) as well as collaboration and communication applications (43 percent), followed by finance and accounting applications (38 percent).

The data most vulnerable to insider threats are customer data and intellectual property (both 57 percent), followed by employee data (45 percent) and financial data (43 percent). Despite this growing challenge, only 25 percent of enterprises monitor abnormal user behavior in the cloud.
“The rapid adoption of cloud and mobile technologies is driving a sharp rise in insider threats at organizations dealing with sensitive data,” said Nat Kausik, CEO, Bitglass. “Countering insider threats requires greater visibility and control of data that has moved beyond the firewall.”