Windows Live ID scam targets personal information
Kaspersky Lab experts are warning of a new scam that uses Windows Live ID as bait to catch personal information stored in user profiles on services like Xbox LIVE, Zune, Hotmail, Outlook, MSN, Messenger and OneDrive.
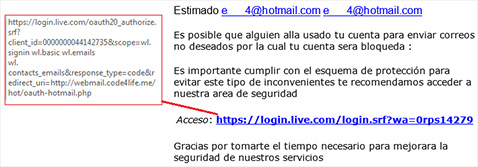
What appears to be a typical phishing email is actually an email that goes to the Windows Live website, with no apparent attempt to get the victims’ logins and passwords. So what’s the trick?
- After following the link and authorizing the account, users received a prompt: an application requested permission to automatically log into the account, view the profile information and contact list, and access a list of the users’ email addresses.
- Scammers gained access to this technique through security flaws in the open protocol for authorization, OAuth.
- Users who click “Yes” don’t give away their login and password credentials, but they do provide their personal information, the email addresses of their contacts and the nicknames and real names of their friends.
This information is most likely to be used for fraudulent purposes, such as sending spam to the contacts in the victim’s address book or launching spear phishing attacks.
“We’ve known about security flaws in the OAuth protocol for quite a while: in early 2014, a student from Singapore described possible ways of stealing user data after authentication. However, this is the first time we have come across fraudsters using a phishing email to put these techniques into practice. A scammer can use the information intercepted to create a detailed image of users, including information on what they do, who they meet and who their friends are, etc. This profile can then be used for criminal purposes,” said Andrey Kostin, Senior Web Content Analyst at Kaspersky Lab.
Developers of Web applications for social networks which use the OAuth protocol are advised to:
1. Avoid using open redirects from your sites.
2. Create a white list of trusted addresses for redirects performed using OAuth, because fraudsters can perform a hidden redirect to a malicious site by finding an application that can be successfully attacked and changing its “redirect_uri” parameter.