Key trends and opportunities in the information security profession
Companies and organizations are increasingly struggling to manage threats, avoid errors and are taking longer to recover from cyberattacks. The results of the (ISC)2 Global Information Security Workforce Study (GISWS) conducted by Frost & Sullivan reveal that the security of businesses is being threatened by reports of understaffed teams dealing with the complexity of multiple security technologies.
In this year’s survey, 62 percent of respondents (up from 56 percent in 2013) reported that their organizations have too few information security professionals, despite budgets allowing for more personnel.
Frost & Sullivan estimate that the global workforce shortage will widen to 1.5 million in five years; with the variety and sophistication of cyber-threats expected to continue, and a broadening footprint of systems and devices requiring security oversight. Signs of strain, including configuration mistakes and oversights, were identified as a material concern. Recovery time following system or data compromises is steadily getting longer.
Security spending is increasing across the board for technology, personnel and training. Further, companies are planning to invest more in tools and technologies. However, complexity due to threats evolving faster than vendors can advance their products led two-thirds of respondents to suggest that a new phenomenon known as “technology sprawl†is undermining effectiveness.
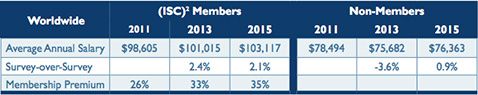
Given this and other challenges faced by hiring managers—45 percent are struggling to support additional hiring needs—the use of outsourcing, managed and professional services, and cloud services are also increasing.
“Many of the facets discovered in this year’s workforce study demonstrate that aspects of the information security program are being carried out in IT departments and other business units – positioning IT as a force multiplier” said David Shearer, CISSP, PMP, executive director, (ISC)2. “Year after year, the study has shown a workforce shortage; but now, we’re finding that the shortage is being compounded with issues that are becoming more prevalent, such as configuration mistakes and oversights that can be detrimental to the security posture of global businesses.â€
Key findings include:
- Only one-fifth of global respondents said that remediation time following a system or data compromise would occur within one day. This is a significant decrease from the 2011 GISWS, which found one-third of respondents reporting the same.
- Application vulnerabilities and malware were identified as top security threats for the third study in a row. For the most part, application security scanning is only conducted post production.
- Phishing is the top threat technique employed by hackers, yet the results showed a decline in importance of awareness training.
- The number of respondents predicting spending increases for security technologies (45 percent) is the highest percentage reported since the study launched in 2004.
- Over 70 percent of respondents identified network monitoring and intelligence, and improved intrusion detection as technologies that significantly improve security. Over half (58 percent) identified that they have implemented, are implementing or are evaluating advanced analytics for detection of malware.
- Lack of in-house skills is the top reason for outsourcing; while a move to outsourcing and managed services was identified as a strategy for tackling technology sprawl by nearly one-third of respondents.