Emerging trends in cyber-attack methodology
Websense documented the latest shift in complex attack trends, evolution in the threat ecosystem and shifting motivation of cyber-attacks.
“Cybercriminals continue to evolve their attack planning and execution to stay ahead of most existing security measures,” said Charles Renert, vice president of security research for Websense. “While the determined, persistent attackers continue to have success in advanced, strategic attacks using zero-day exploits and advanced malware, there has also been a boom in cybercriminal activity on a massive scale. Even these more ‘common’ forms of attack are easily slipping past organizations without real-time defenses.”
The Websense Security Labs 2014 Threat Report details the growing global criminal-infrastructure-as-a-service economy through exploit kits and compromised websites redirection chains. Through an analysis of the latest attack methodology, Websense security researchers analyze the seven threat stages of advanced attacks. In addition, outcomes include the modification and repurposing of existing malware source code.
Key findings include:
- 85 percent of malicious links used in web or email attacks were located on compromised legitimate websites
- 3.3 percent of all spam contained malicious links and other malicious content
- The average number of website redirects used per attack in 2013 was four
- The maximum number of redirects used in a fully documented attack was 20
- Websites classified as Business and Economy, Information Technology, Shopping and Travel made the top 10 list of compromised redirect destination categories
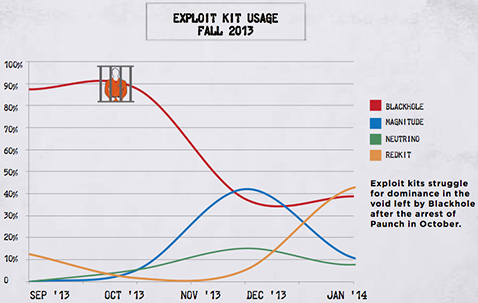
- The Magnitude and Neutrino Exploit Kits experienced the largest surge in adoption following the arrest of Blackhole’s creator
- 30 percent of malicious executable files sampled included custom encryption of command and control communication or data exfiltration.
The report also documents how the infrastructure of an attack campaign is constantly developed, enhanced and reused throughout the entire threat lifecycle.
To avoid detection when reusing components in subsequent attacks, criminals are increasingly taking an approach that involves modification and modulation of existing attack tools. Often, this means choosing to take advantage of a specific strength of a particular piece of malware to target new industries.
In addition, Websense security researchers observed the Zeus malware, which was originally designed as a financial threat and keylogging Trojan, dramatically increased in use as it was repurposed for other vertical markets.
In the last year the government and the communications industry joined financial firms among the top five verticals targeted with Zeus malware. The top two industries hit hardest with Zeus attacks were the services and manufacturing sectors.