Tresorit for Business
 In the cloud computing era, companies need to be proactive on secure collaboration and file sharing. Tresorit for Business is a solution that, among other things, helps organizations with managing, protecting and preventing leaks of their corporate data.
In the cloud computing era, companies need to be proactive on secure collaboration and file sharing. Tresorit for Business is a solution that, among other things, helps organizations with managing, protecting and preventing leaks of their corporate data.
The service provides end-to-end encryption for data in motion, along with all the enterprise functions related to managing user behavior and enforcing the policies for sharing the data in the most secure way possible.
How does Tresorit work?
One of Tresorit’s major advantages is a patent-pending security system where both the encryption and decryption is done on the client side. In the “Snowden era” it is important to note that Tresorit doesn’t store any aspect of the crypto process that could make anyone else able to access your files. Also, the company handles the data under strict Swiss privacy laws. Their datacenters, made disaster proof and protected by 24/7 physical security, are located in the European Union and are HIPAA and ISO27001:2013 compliant.

All files uploaded to the cloud are encrypted, client-side, with AES-256 encryption. File operations are authenticated by using RSA-2048 signatures applied on SHA-512 hashes. Transport Layer Security (TLS) is used between the client’s workstation and the Tresorit cloud service. Invitation and key agreement is done with ICE and ITGDH. The latter is a key management protocol that allows a group of users to agree on a shared group key, which can be used to protect shared data stored remotely in the cloud. For the geek in you, a detailed paper on it was published at the 2012 edition of Parallel Processing Workshops (ICPPW).
Tresorit applications and web access
The Tresorit desktop application is available for Windows and OS X systems, iOS- and Android-running mobile devices, as well as Windows Phone and Blackberry devices. Tresorit is also among the first apps offered on the Blackphone Silent Store.
I’m an OS X user, so I am basing my experience on the Mac version of the product. The installation was pretty straightforward and the application itself looks clean and is easy to use. There aren’t many options here, as the functionality from the client perspective is focused on encrypting and sharing files and managing encrypted links. I’ll go into more details on these links later on.

From a client’s standpoint, generating and storing data begins with creating specific Tresors. Tresors are placeholders for the files that you will manage. Every Tresor corresponds to a local folder, which the user can work with even outside Tresorit.
The files inside the Tresors/local folders are unencrypted, but when they are synched to the cloud, their online versions are encrypted. Versioning history, as well as detailed specifications about activities (added, edited, deleted, etc.) is available for all the files. Tresors shared by other users will become visible inside the application.
One of the things that I considered to be a major negative aspect of Tresorit was fixed just a couple of weeks ago, when the company introduced web access to the encrypted files. If it seems strange that web access is called a new feature in 2015, check out this blog post from 2013, in which security-minded developers of Tresorit specified that they couldn’t guarantee the highest level of security for web access, so this feature was put aside until this could be achieved. A new blog post explains how they implemented the whole “zero knowledge” (your data cannot bee seen by them) concept into the web access interface.
Administration and policies
The administration web interface has three tabs: activity, users and devices, and groups and policies.
Activity: This is a textual and graphical overview on high level Tresorit usage within the organization. There are pie charts with specifics on storage per user, as well as operating systems used. The activity section provides a snapshot of which user logged from what device and IP address. Have in mind that the location is approximate, as it is used based on an IP range and is mostly there to identify possible compromised accounts (i.e. accessed from another country).
Users and devices: Settings related to managing users on your account, checking usage stats and the devices they are using to use Tresorit. From here, every user and their device can be suspended or activated, or they can be added to a specific group.
Groups and policies: Typical set of functions where the administrator can set up rules, such as timeout policies for logged in users, IP filtering, two factor verification, ban specific platforms, etc.

Digital rights management
While I didn’t use and test this option, it’s good to know it exists.
Tresorit DRM complements Tresorit’s existing cloud-storage solution by offering more control to businesses by extending security to documents once they have been shared, and during collaboration. The DRM aspect of Tresorit is powered by the Microsoft Windows Rights Management Services (RMS) technology. By using DRM enabled Tresors, senders and receivers are prevented from saving, printing, copying or taking screenshots of DRM protected files.
Two-factor authentication
With the majority of data moving online, two-factor authentication is a function that every service of this type should provide to users. Tresorit offered the two-step verification option for Business users in November 2014.
The service can be enabled from the “Security” tab of the account settings and will become active the next time you log in manually or install Tresorit on a new device. I stressed the phrase “log in manually,” because you can access the web based admin interface without authenticating by clicking a link from the Tresorit application. This link is, of course, not static.

Two-step verification options include a mobile app (such as Google Authenticator for iOS), text message to a cellular phone, voice call, and email. If you enable the mobile application, the system will automatically add the email option by default. As it is stated: “For security reasons you must have two active options for 2-Step verification. If you deactivate this option, we will no longer ask for your authentication code when you sign into your account.”
I understand that this is probably enforced because of usability, but for those of us who are paranoid, this could be viewed as a security risk. Mobile app, voice call or text message are authentication methods that are (at least) a bit harder to compromise then email, so automatically adding email as an alternative to a mobile authenticator is subpar.
Encrypted links
I’ve been using the Tresorit service for a couple of months now and one of the things I enjoying on a daily basis is a seamless, secure file-sharing process called Encrypted links. When sharing files over email, and especially larger files, I used to use one of the cloud data service providers such as Box.com or Dropbox. This is a good solution for low-key data files, but I never uploaded anything remotely personal in unencrypted form. Even though those are legitimate businesses, we all know that there are a number of risk factors with data that is stored in the cloud without an extra layer of security. SSL access to the service doesn’t cut it.
Tresorit provides a good alternative with Encrypted links, because you can simply “right click” on any file on the computer and create an encrypted cloud copy of it instantly. You can set up an expiration date for the link, limit the number of times the file can be downloaded (I always use 1 when sending a file to someone; you never know who is “out there”) and you can even password-protect the file for extra protection.
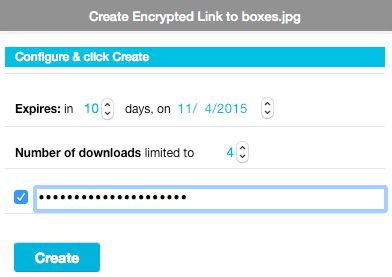
The newly created link is automatically copied to your clipboard and is ready to use. With the latest update, Tresorit finally changed the look of the links: a month ago the link would be very long (typically around 240 characters), and now they use a shortened version (just over 40 characters) that looks much better when you send it via email. (A three-line-long web link with “random” characters? XSS was always the first thing on my mind.)
These linked files use the same encryption as the “regular” Tresorit synched files, but the system creates a temporary decryption environment – a lightweight version of Tresorit – in the recipient’s web browser. From a technical point of view, this is done in a way that makes sure that the Tresorit server cannot access the sent data and the data can only be decrypted by the recipient on her end.
The Encrypted link option is currently not available in all web browsers. The company specified that older Internet Explorer browsers are not supported due to security reasons, and on my OS X, I cannot use Safari with it – just Chrome and Firefox. It should be noted that Javascript has to be enabled for the browser decryption process. Opening encrypted links on some mobile devices is potentially possible, but not currently officially supported.
All of the encrypted links you’ve created will be listed in the appropriate section of the Tresorit application.
Pricing
Tresorit for Business is priced at 20 EUR per month for an organization of up to 200 users. This includes 1000GB storage per user, unlimited sharing and activity history, remote wiping of documents, priority support and live training. Enterprise plans for larger organizations can be set up with the sales team.
Final thoughts
Tresorit for Business is a great product that is simple to use and provides a high level of security for data in transit. The system is being developed actively, so every now and then new features are released. Security is obviously extremely high on the list of priorities of the Tresorit team, and I will definitely keep using it.