Exploit kit activity up 75 percent
The creation of DNS infrastructure by cybercriminals to unleash exploit kits increased 75 percent in the third quarter of 2015 from the same period in 2014, according to Infoblox.
Exploit kits are a particularly alarming category of malware because they represent automation. Highly skilled attackers can create exploit kits, which are packages for delivering a malware payload, and then sell or rent these toolkits to those with little technical experience – vastly increasing the ranks of malicious attackers capable of going after individuals, businesses, schools, and government agencies.
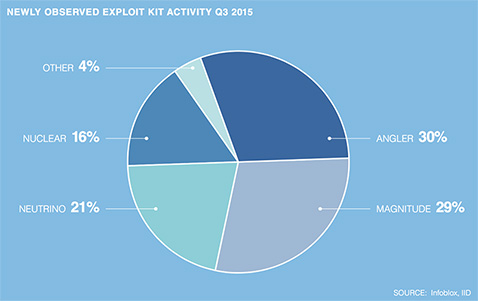
Four exploit kits – Angler, Magnitude, Neutrino, and Nuclear – accounted for 96 percent of total activity in the category for the third quarter.
Most exploit kit attacks are distributed through spam emails or compromised web sites, or are embedded in online ads. When users click a link in the emails or ads, the exploit kit takes advantage of vulnerabilities in popular software to deliver a malware payload that can perform actions such as planting ransomware, capturing passwords for bank accounts, or stealing an organization’s data.
Cybercriminals need the DNS to register domains for building the “drive-by” locations where exploit kits lie in wait for users, and for communicating with command-and-control servers that send instructions to infected devices and extract information.
“Exploit kits are behind some of the highest-profile attacks in recent months,” said Craig Sanderson, senior director of security products at Infoblox. “For example, a recent Angler attack on Mail Online implanted malicious ads on the site for five days, potentially exposing millions of online visitors to infection.”