The top three banking malware families
“The primary motivator behind banking malware attacks is to capture credentials, financial data, and personal information from employees, and partner company employees, across industries. Then apply this stolen information in fraudulent wire transfers or fake automated clearing house (ACH) transactions to steal funds.
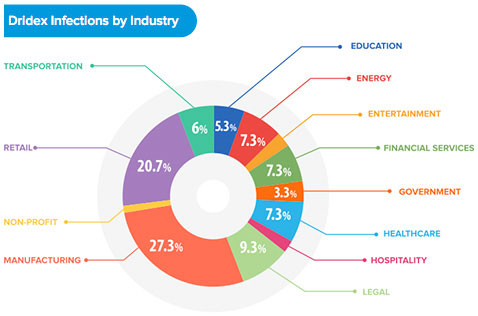
SecurityScorecard sinkholes found 11,952 infections affecting 4,702 organizations and identified the top banking malware families to be Dridex, Bebloh and TinyBanker:
- These malware families are simple in functionality which is proving to be more profitable than more complex techniques and methods, such as taking antiquated, bloated code bases from third party malware coders.
- Dridex is the most prolific Trojan being circulated within the corporate sector.
- The use of banking malware is not limited to large financial institutions, though they remain the primary targets.
- Dridex spreading campaigns appear to be orchestrated by more advanced actors with an interest in targeted attacks.
- The healthcare industry experienced lowest rate of Bebloh infections, but did not experience the same rate of infection as other industries.
“Security awareness and education is never enough. The evolving tools, techniques, and procedures that are continuously honed by malicious actors make it nearly impossible for every individual in an enterprise to be aware of the latest attack method,” said Alex Heid, Chief Research Officer of SecurityScorecard. “To prevent financial losses from an attack, businesses need a closed loop of communication between partners, suppliers, and all third parties that are impacted by banking malware. It is critical that companies think about their collective information security ecosystem when gauging their own security risk.”
The top three banking malware families being captured are all direct variants of Zeus, or mimic Zeus-like functionalities. These malware attacks are the preferred method of obtaining stolen credentials, especially when traditional attacks on web applications or network-based attacks are being monitored by internal security teams.”