Operation Emmental exploits holes in banking security
Trend Micro researchers have discovered and analyzed a clever attack aimed at customers of Austrian, Swiss, Swedish, and Japanese banks. They dubbed it Emmental, after the famous Swiss cheese, because the online banking protections these banks use are similarly full of holes.
This particular attack starts with fake emails purportedly coming from locally popular retailers and ostensibly carrying a receipt. Those recipients who download and run the file, and allow it install a fake Windows update tool, have actually allowed DNS-changing malware to infect their computer.
This piece of malware changes the system’s Domain Name System server settings to point to one that is under the attackers’ control, which hosts spoofed online banking login pages of a number of banks in the above mentioned countries. The malware also installs a new root SSL certificate so that these phishing sites won’t be detected as malicious by the users’ browser.
Finally, the malware deletes itself. “This means that if the infection attempt was not immediately detected, any anti-malware check that follows will not detect anything since the file will no longer be there,” Trend Micro researchers pointed out.
When the victims try to visit their online banking login pages, they are redirected to the spoofed ones. The usernames, PINs and bank account numbers they enter into them are now in the hands of the attackers.
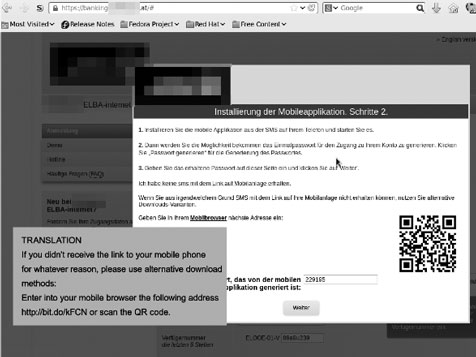
Since they didn’t receive the bank’s one-time password via SMS, they are urged to download a fake session token generator app (click on the screenshot to enlarge it):
The token provided by the app is accepted by the fake page, and the victims believe that their transaction has been effected.
In the meantime, the crooks use the collected login credentials on the legitimate online banking websites and, once the bank sends the OTP to the victims’ phone, the fake app intercepts it and sends it to the criminals, who then have the final piece of the puzzle needed to access the victims’ account.
“Emmental is an attack that has very likely evolved over time. The fact that the most salient part of the attack—the PC malware—is not persistent likely helped the attackers keep a low profile,” the researchers noted.
“The infrastructure required to pull the attack off is not inconsequential—the attackers need a Windows malware binary, a malicious Android app sporting various banks’ logos, a rogue DNS resolver server, a phishing Web server with several fake bank site pages, and a compromised C&C server.”
Some details point to the attackers being from Russia and/or Romania.
“Operation Emmental’s complexity highlights the high value that criminals place on active bank account information,” commented Chris Boyd, malware intelligence analyst at Malwarebytes.
“The multi-platform method shows the increasing sophistication of cyber-criminals and their willingness to adapt and combine existing techniques. The use of a piece of malware which removes itself once it has completed its primary objective, in addition to a piece of Android malware which is designed to intercept one time passwords from the bank itself gives you a pretty sophisticated attack which is hard for the average online banking user to spot.”
“One could argue that having such a complicated chain of events could work in a potential victim’s favour – if just one part of the multi-step heist fails, then the whole scheme could fall flat,” he noted. “Despite this, I think we will see more of this type of cross platform approach which blends social engineering, multiple platforms and sophisticated obfuscation.”