Google Code hosting malware-spreading project
Google Code’s project hosting feature has occasionally been used by malicious individuals for storing and spreading malware.
Zscaler pointed out yesterday that even though Google claims that any project including malicious files will be taken down, it takes the Google Code team a rather long time to detect them by scanning the hosted content.
Take this project discovered by Zscaler as an example:
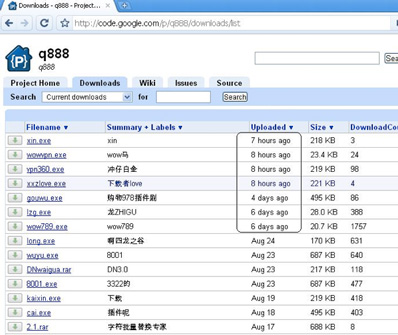
Most of the files are executables or .rar archives. The first uploaded file dates back to June 24, and more have been uploaded throughout August.
Taking the first file on the list (xin.exe) and testing it on VirusTotal showed that only 8 out of 43 solutions were able to detect it. The second file (wowvpn.exe) is detected by more than half of the solutions.
Further analysis showed that if xin.exe was executed on a system, it would try to download other malware hosted on this project site through a series of GET requests.
The security researchers analyzed the rest of the files, and concluded it is a collection of Trojans, keyloggers, backdoors, and other malware. An analysis one of the files with ThreatExpert points to China as the country of origin.
After this discovery was made public, Google removed the offending project. But this instance shows that the company must find a better way of detecting malware hosted on its sites.