Instant messenger phishing made simple
An Internet application “comes to the rescue” of MSN & YIM users who want to find out if their friends, colleagues or acquaintances have blacklisted them.
It is not easy to stay on top of the game 24/7 especially when your social network profiles start to pile up and the number of followers is on a constant rise. As each social community member is placed at the center of a spider web of connections, one of the ways in which they can manage an otherwise chaotic world of “friends and friends’ friends” would be to find out if they themselves have been banned, blacklisted or erased from their contacts’ lists.
These particularly active MSN & YIM users are targeted by an extremely ingenious social-engineering scam. All they have to do is to write in the Blocked or Not Internet page their account IDs and passwords with the naive intent of keeping track of those who still have them in their lists or not.
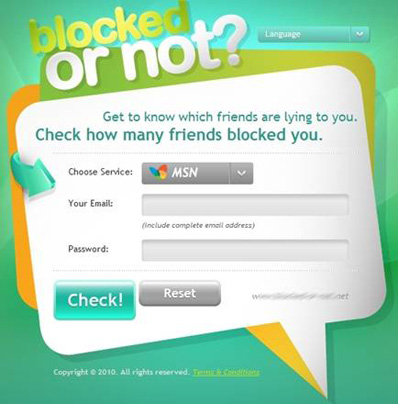
Once the credentials are logged in, the curious user is a click away from discovering the “lying” friends that blacklisted them.

Fortunately, the answer is comforting as invariably none of the curios user’s friends will have blocked them during the past two months.

And now, the payload: on the one hand, there’s the IDs and passwords collector that harvests a considerable number of account credentials to be used in various illegal actions, such as money grabbing scams, spam attacks, or impersonations. And there’s more: the stolen data enables the scheme’s authors to pry into personal conversations, connect the YIM/MSN IDs to other user accounts and even to reset e-banking passwords.
On the other hand, the moment users are festively informed that their friends are loyal; they are redirected to an advertisement page that provides a wide assortment of offers such as free on-line movies, surveys and games. The games actually turn out to be sex chat rooms and none of these items are free.
It seems that asking users to fill in surveys is quite a lucrative strategy, since it is now used on a large scale as a primary way of squeezing revenue out of website traffic. This is the same approach used recently as part of a Facebook clickjacking scam.
However, should users yield to the temptation of clicking one of the appealing options; they are immediately suggested to install a piece of adware (a toolbar). This will eventually change the start-up page and the default search engine with the illicit intent of monitoring the respective users’ browsing habits. The ultimate aim is to build users’ buyer profiles and to make possible a more targeted distribution of ads.

Interesting enough, the cyber-criminals behind this scheme have taken extra precautions and blocked access to the webpage by blacklisting the IP ranges associated with the BitDefender labs.

Author: Loredana Botezatu, BitDefender.