Don’t sink your network
 Too many of today’s networks are easy to sink. One attack pierces the perimeter, and all of the organisation’s most sensitive data comes rushing out. Soon after, their logo is slapped across the evening news as the pundits start circling the water.
Too many of today’s networks are easy to sink. One attack pierces the perimeter, and all of the organisation’s most sensitive data comes rushing out. Soon after, their logo is slapped across the evening news as the pundits start circling the water.
Modern ships are not built under the assumption that their hull is too strong to breach. In fact, they are designed to contain a breach as quickly as possible to keep the entire vessel from going under. Organsations can adopt this philosophy to make sure that one intrusion doesn’t compromise all of their data.
Network segmentation functions by cordoning off resources and users by role to limit the reach of an intruder. In an unsegmented network, everyone has access to everything. By dividing these different groups into separate areas it limits their access and the overall security posture of the organisation is improved.
We can compare it to compartments on a ship. When the ship is healthy, all of the different compartments operate in concert with one another. But in the event of a hull breach or flooding, the affected compartments seal off from the others to contain the water. If it is working as intended, then the water is contained and the ship is able to maneuver to a safe location to perform repairs. It isn’t perfect – most famously illustrated by the Titanic – but it is effective most of the time.
In a segmented network, normal business functions are unimpeded as everyone has access to what they need. But in the event of an attack, the threat actor is confined to whichever segment is compromised, drastically reducing the amount of sensitive material obtainable.
Segmentation also improves visibility and threat detection by providing more points of monitoring. As traffic crosses segmentation borders, it can be inspected and audited, giving the security team insight into what is happening on the ground.
This is in stark contrast to an attack on an unsegmented network, where the attacker is able to move laterally across the entire network. In that time, they are able to identify all of the sensitive data and take advantage of every vulnerability that might be present. This results in an attack that is able to quickly pilfer anything valuable while also leaving more opportunity for persistence and a continuous compromise.
What’s the problem?
Historically network segmentation has had two major flaws; it required too much effort and maintenance, and wasn’t scalable. It relied on extensive access control lists, and points of enforcement had to be updated individually every time there was a change in policy.
Another drawback of traditional segmentation was the difficulty of testing and implementing it. Few organisations are aware of every valuable resource that resides on the network, and fewer still understand what resources are needed by users to perform their job. This often forced administrators to segment based on intuition, which almost always resulted in weakened security or disruption to day-to-day business.
What was required to make segmentation practical was a platform that is easy to manage, the network insight necessary to craft effective policies and a process to maintain integrity in dynamic environments. Thanks to advancements in technology and methodology, these things are now practical for even the largest networks.
A new era of segmentation
The advent of software-defined segmentation made great strides in bringing segmentation to large, modern networks. It functions by abstracting security policies away from hardware terms, making crafting policies much easier to understand whilst maintaining integrity even in fluid network environments.
Software-defined segmentation facilities centralised management. Instead of manually updating policies on every network infrastructure device individually, administrators can design and change policies in one location before pushing it out to all points of enforcement simultaneously. This method reduces the amount of man-hours required to maintain segmentation and ensures policies are up to date network-wide.
A new methodology for a new era
Even with these capabilities, segmentation can be a complicated process. Organisations are dynamic beings. They grow and change. To keep up, segmentation policies must be continuously evaluated and tweaked to remain relevant.
The key to this challenge lies in active segmentation, a methodology designed to efficiently identify changes within the network and adapting policy to match. Based on the OODA Loop, active segmentation is a cyclical process of observing network behavior, orienting segmentation goals to that behaviour, adapting policies and implementing them.
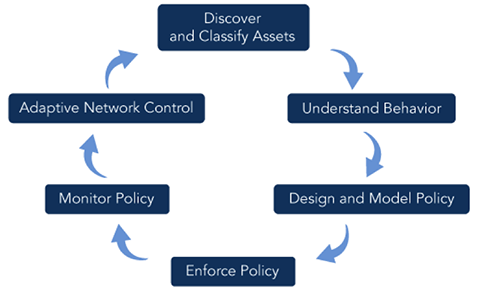
This process would be a tall order, except much of it can be streamlined using network visibility tools. The beauty of comprehensive visibility is you can implement soft policies that can trigger alerts when certain traffic is observed. Administrators can quickly identify new machines and test run policy changes before enforcing them.
Flood-proof your network
The ever-evolving threat landscape and sophistication of cyber attackers make relying solely on traditional perimeter defense ineffective. The good news is the battle isn’t lost at the initial compromise. Like ships contain flood water, networks can be designed to confine intruders to a small area, preventing a breach from spreading.
Shoring up internal defences and making your network inhospitable to intruders can drastically reduce the time to identify a threat, providing a window of opportunity to security personnel. Through new technologies and proper segmentation techniques, organisations can hinder lateral movement and contain the consequences of a breach. If done correctly, attackers have access to less data and are able to be identified before they can cause damage.