Top 5 Security and Networking Widgets for Mac OS X
This article presents 5 widgets that that enable you to perform various tasks quickly, straight off the Dashboard.
AirTrafficControl

AirTrafficControl is the most advanced wireless networking widget available.
- Connect to any type of network.
- Sort networks by any feature.
- View current connection details including network speed.
AirTrafficControl now can access the Keychain where wireless network passwords are stored. If you would like to connect to a network simply click on it. If you have the password in your Keychain AirTrafficControl will connect automatically. If you need to type in the password AirTrafficControl will put it in the Keychain so that Apple’s built in networking software can find it later.
ladyCrypt

ladyCrypt makes it easy to convert simple words to secure passwords. It lets you customize the encoded string: lowercase or uppercase and final string length. You can also copy your newly generated (secure) password to the clipboard in one click. The widget supports SHA1 encryption.
Dash Shredder

This widget will completely erase files and folders beyond any recovery in compliance with the US Department of Defense specifications for removing sensitive data from a storage device. When a file is removed with the shredder, you can never recover it so be careful.
UNIX Permission Calculator

The UNIX Permission Calculator lets you convert between different representations of UNIX-style permissions: The numerical style, the textual style and a set of checkboxes. This widget is aimed at Mac users that want to learn more about the UNIX underpinnings of OS X.
Hashapass
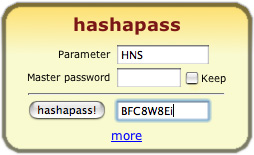
Hashapass utomatically generates strong passwords from a master password and a parameter. So for example, you can generate a different password for your webmail account, another one for a web service and you just need to remember one password. When you are not using your regular machine, you can go to hashapass.com and find a form that will help you recover your password safely, and without transmitting your password over the Internet.